Comprehensive Cloud Services: Empowering Your Digital Change
Comprehensive Cloud Services: Empowering Your Digital Change
Blog Article
Secure and Reliable: Taking Full Advantage Of Cloud Services Benefit
In the fast-evolving landscape of cloud solutions, the crossway of protection and efficiency stands as a critical point for companies seeking to harness the complete possibility of cloud computer. The balance in between safeguarding information and ensuring streamlined procedures calls for a tactical strategy that necessitates a deeper exploration right into the complex layers of cloud solution administration.
Information Encryption Ideal Practices
When implementing cloud services, employing robust information security best practices is vital to guard sensitive information successfully. Data security includes inscribing information in such a method that just licensed events can access it, ensuring discretion and safety and security. Among the fundamental finest practices is to utilize strong encryption algorithms, such as AES (Advanced Encryption Requirement) with secrets of sufficient size to safeguard information both in transportation and at rest.
Moreover, implementing correct crucial administration strategies is important to preserve the protection of encrypted information. This consists of safely producing, saving, and turning encryption secrets to stop unapproved access. It is also essential to encrypt information not only during storage however likewise during transmission in between individuals and the cloud solution provider to prevent interception by harmful stars.

Resource Appropriation Optimization
To maximize the advantages of cloud services, organizations must concentrate on optimizing source appropriation for reliable procedures and cost-effectiveness. Resource appropriation optimization entails tactically distributing computing resources such as refining storage space, power, and network transmission capacity to fulfill the differing needs of applications and work. By executing automated resource allowance systems, companies can dynamically adjust source circulation based upon real-time demands, making certain ideal performance without unneeded under or over-provisioning.
Efficient resource allocation optimization causes boosted scalability, as resources can be scaled up or down based on use patterns, causing boosted flexibility and responsiveness to transforming service requirements. By properly straightening sources with work needs, organizations can reduce operational expenses by eliminating waste and maximizing use performance. This optimization likewise improves overall system reliability and resilience by stopping source traffic jams and making certain that essential applications get the necessary resources to operate efficiently. Finally, resource allotment optimization is necessary for organizations seeking to take advantage of cloud solutions efficiently and safely.
Multi-factor Verification Implementation
Applying multi-factor verification enhances the safety and security position of companies by calling for extra confirmation actions past simply a password. This added layer of protection considerably decreases the risk of unapproved access to sensitive data and systems. Multi-factor authentication usually integrates something the user recognizes (like a password) with something they have (such as a smart phone) or something they are (like a finger print) By incorporating multiple elements, the likelihood of a cybercriminal bypassing the authentication process is considerably reduced.
Organizations can pick from different methods of multi-factor verification, consisting of text codes, biometric scans, equipment symbols, or verification applications. Each approach supplies its very own degree of safety and security and convenience, allowing services to select the most suitable alternative based upon their distinct demands and sources.
Additionally, multi-factor verification is vital in protecting remote accessibility to cloud solutions. With the enhancing pattern of remote job, ensuring that only authorized workers can access vital systems and information is vital. By carrying out multi-factor authentication, organizations can fortify their defenses against possible safety violations and information burglary.

Catastrophe Recovery Preparation Techniques
In today's digital landscape, effective calamity recovery preparation techniques are vital for companies to alleviate the effect of unexpected interruptions on their data and procedures honesty. A robust calamity healing plan entails recognizing prospective risks, evaluating their prospective effect, and carrying out aggressive steps to guarantee service connection. One vital facet of calamity recuperation preparation is producing back-ups of critical information and systems, both a knockout post on-site and in the cloud, to allow speedy remediation in situation of an incident.
Additionally, organizations should perform normal screening and simulations of their calamity recovery treatments to recognize any kind of weaknesses and boost response times. It is likewise important to develop clear interaction methods and mark accountable individuals or groups to lead recovery efforts throughout a situation. Additionally, leveraging cloud services for disaster healing can offer flexibility, cost-efficiency, and scalability contrasted to conventional on-premises solutions. By prioritizing catastrophe healing preparation, companies can lessen downtime, secure their online reputation, and keep functional strength when faced with unanticipated occasions.
Efficiency Checking Tools
Efficiency surveillance tools play an important role in giving real-time insights into the health and wellness and effectiveness of a company's systems and applications. These tools allow services to track various performance metrics, such as reaction times, resource usage, and throughput, allowing them to determine bottlenecks or possible problems proactively. By continually keeping track of essential performance indicators, companies can make certain optimum performance, identify patterns, and make informed decisions to boost their general operational performance.
An additional commonly utilized tool is Zabbix, supplying monitoring abilities for networks, servers, virtual machines, and cloud services. Zabbix's easy to use user interface and personalized functions make it a valuable property for companies seeking durable efficiency click here for more info tracking solutions.
Final Thought
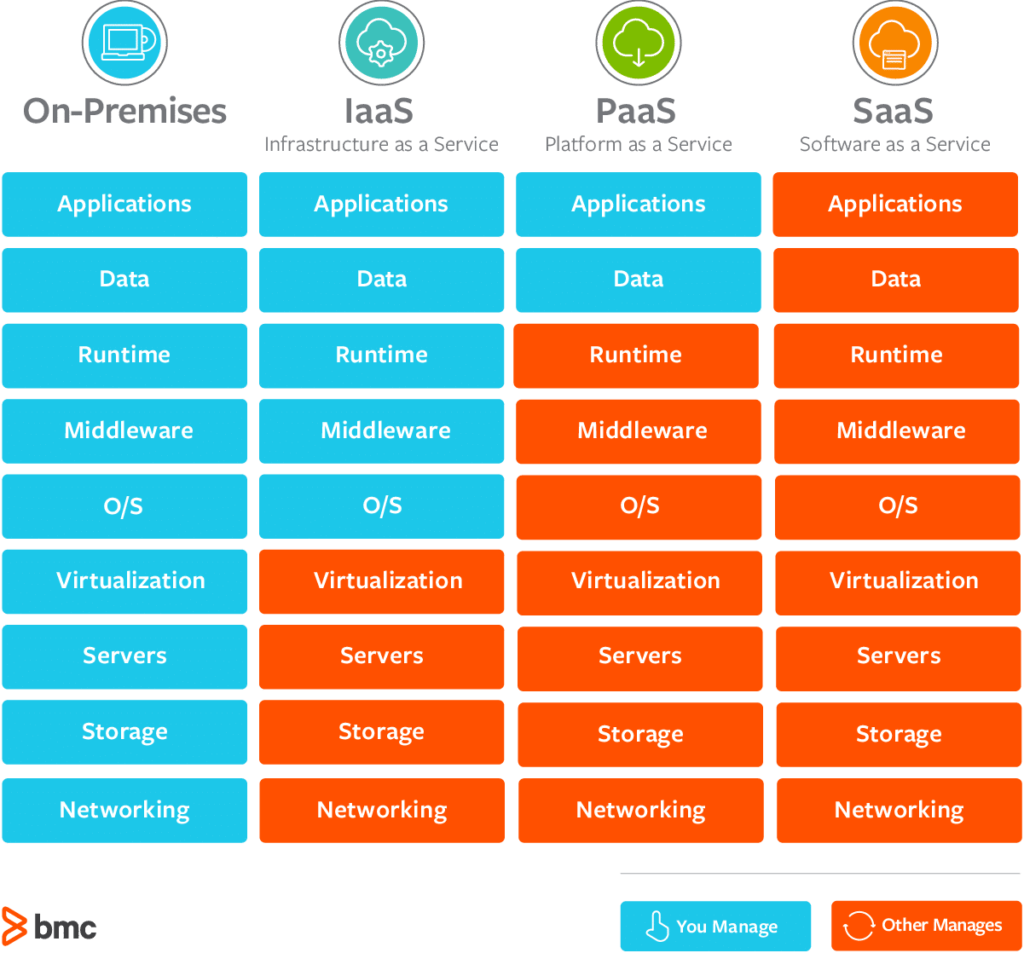
In the fast-evolving landscape of cloud solutions, the crossway of security and performance click here now stands as an important point for organizations looking for to harness the full potential of cloud computing. The equilibrium in between guarding data and ensuring streamlined operations calls for a tactical approach that requires a deeper expedition into the detailed layers of cloud solution management.
When carrying out cloud solutions, using durable information file encryption finest techniques is extremely important to guard delicate details successfully.To maximize the benefits of cloud solutions, companies have to concentrate on optimizing resource allowance for effective procedures and cost-effectiveness - linkdaddy cloud services. In conclusion, source allocation optimization is vital for companies looking to utilize cloud services successfully and safely
Report this page